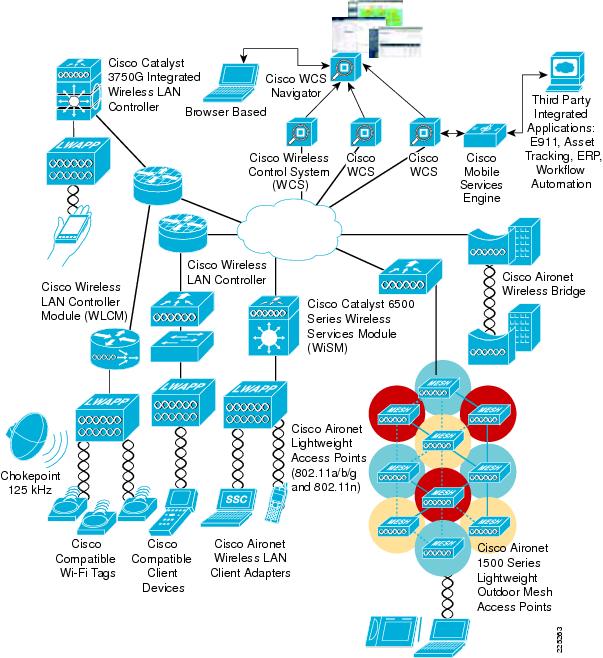
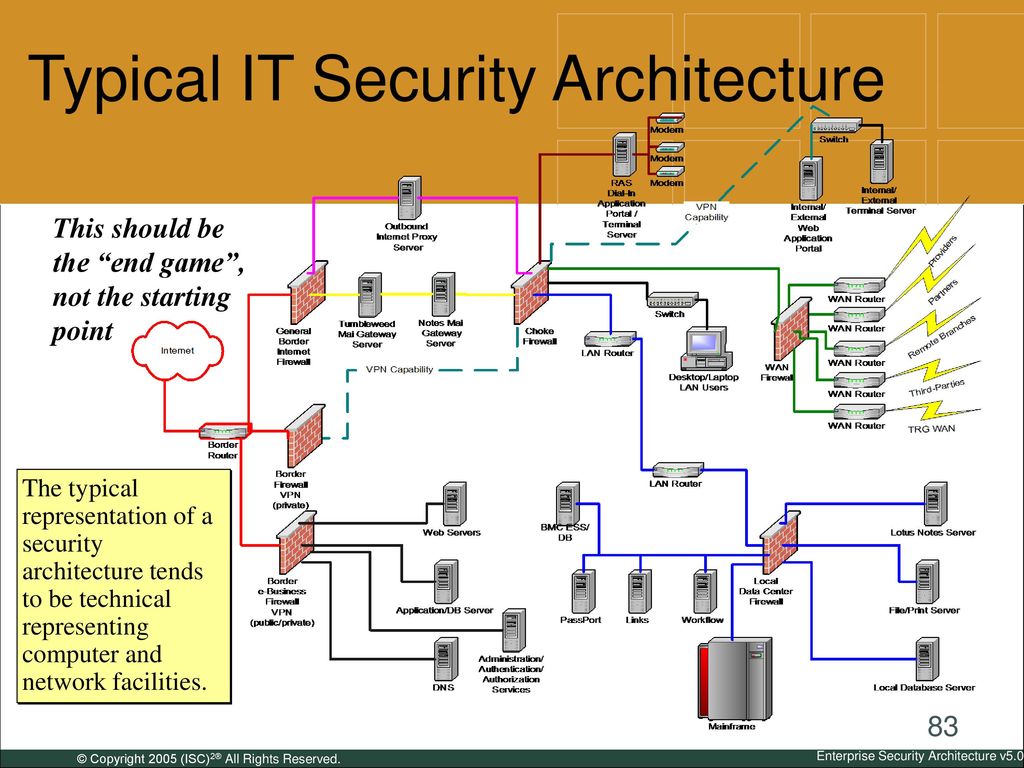
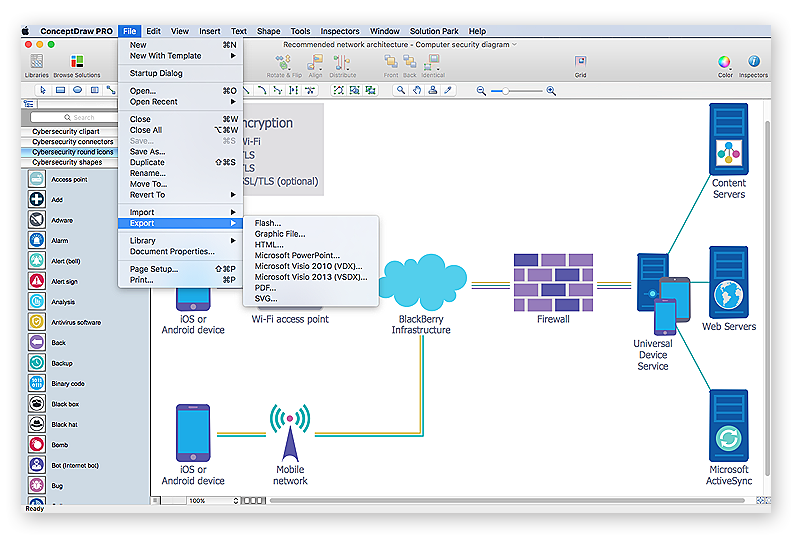
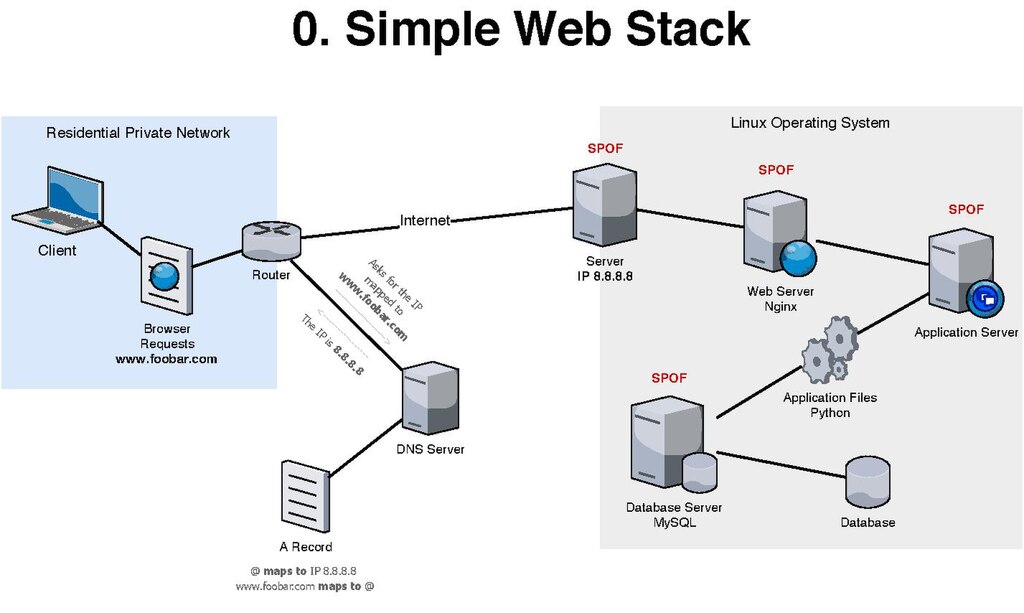
38 network security architecture diagram
The 5G core uses a cloud-aligned service-based architecture (SBA) to support authentication, security, session management and aggregation of traffic from connected devices, all of which requires the complex interconnection of network functions, as shown in the 5G core diagram. We have seen these diagrams used for several purposes including. Starting template for a security architecture - The most common use case we see is that organizations use the document to help define a target state for cybersecurity capabilities. Organizations find this architecture useful because it covers capabilities across the modern ...
Purpose. (1) This transmits revised IRM 2.15.1, Enterprise Architecture (EA), Enterprise Architecture (EA) Overview. The purposes of this IRM are to: Define the EA and depict the key components of EA. Define how the EA fits within the concept of operations for the business.

Network security architecture diagram
October 24, 2021. High Level Example Of Hub And Spoke Vdc Networking Cloud Infrastructure Cloud Diagram. Microsoft Azure Architecture Solution Azure Computer Network Solutions. Azure Network Diagram Use Azure Diagram Tool By Creately To Draw Your Azure Network Diagram Azure Network Diagram Tool Hel Diagram Fuse Box Widebody Ferrari. Microsoft online services systems, dependencies, and external connections are documented in Microsoft online services' information security architecture. Both the information security architecture and corresponding data flow diagrams are reviewed and updated annually at a minimum, as well as whenever significant changes are made to the system. Hence, this network architecture design is recommended for customers wanting to adopt Cloud Adoption Framework data management and analytics. If extra network policies need to be enforced within the data platform, it's advised to use network security groups instead of central network virtual appliances. Meshed network architecture conclusion
Network security architecture diagram. AWS Network Architecture Diagrams. ... AWS Security Architecture Diagram. With the Hava security group diagram you can view all of your configured security groups with the open ports overlaid to enable an instant visual snapshot of the traffic flow, ingress and egress points. The security group diagram being interactive ensures you can select a ... A network architecture diagram, also known as a network infrastructure diagram, helps admins visualize their complete network infrastructure and architecture. It provides a comprehensive picture of resources and network layers, potentially including hardware, layout and topology, wireless connections, software, protocols, and more. This is one of those key principles of a zero trust architecture we just mentioned: micro-segmentation. To implement a cybersecurity mesh, security policies have to apply at the identity level, the individual level versus at the network level by using firewalls, checking IP addresses and controlling ports. This ensures that resources are secure ... There is no question that keeping accurate GCP architecture diagrams is essential for well managed and easily communicated network infrastructure.. Having up to date diagrams on hand allows you to easily understand the design and operation of your Google Cloud architecture and gives you the ability communicate your network design at all levels of your organisation.
Architecture Diagram. Let's discuss this above architecture. In the Networking layer, it has one VPC (Private network in cloud), 9 subnets, Internet Gateway, and Nat Gateway. It also has components of compute layer, such as load balancer, EC2, Jump Host (Bastion Server) databases etc to explain the architecture. Subnets. Symbols of Network Architecture. Pre-made and standard network diagram symbols are very helpful for network engineers when they need to design and demonstrate their network architecture. Edraw Max provides a lot of basic network architecture symbols, which helps you build and read a complex network diagram. Network and Peripherals. N etwork architecture is the physical and logical design of a computer network. This framework is often represented with a diagram to provide the precise description of an established network, and the system is designed by the network architect with the help of network engineers. Present your network audit report and make audit suggestions to appropriate stakeholders. Once your auditing team has completely diagrammed your network architecture and found potential weaknesses in security, compliance, and efficient operations, it is time for that team to produce their final network audit report.
Secure Socket Layer (SSL) provides security to the data that is transferred between web browser and server. SSL encrypts the link between a web server and a browser which ensures that all data passed between them remain private and free from attack. Secure Socket Layer Protocols: Attention reader! Don't stop learning now. implementing a continuous security improvement process, creating and evolving a network security maturity model, developing and maintaining network architecture diagrams and documentation, ensuring no default settings or passwords for network devices, and; implementing a patch and vulnerability management program for network infrastructure devices. Using EdrawMax to create your own AWS architecture diagram in minutes. If you have had Edraw installed, you can create a more detailed AWS diagram by using the AWS Architecture diagram templates. Step 1: Open EdrawMax desktop software or EdrawMax web-based application . Step 2: Navigate to [ New] > [ Network] > [ AWS] in EdrawMax. Segment your network footprint and create secure communication paths between segments. Align the network segmentation with overall enterprise segmentation strategy. Design security controls that identify and allow or deny traffic, access requests, and application communication between segments. Protect all public endpoints with Azure Front Door ...
Network security. In order to expand on the topic of security and network traffic, we need to dive into network security. ... This will make more sense once you see the detailed architecture diagram. :police_car_light: Alert, one common issue I see people facing is their Spark pools not being able to read files on the storage account. This is ...
A network security group (NSG) contains a list of Access Control List (ACL) rules that allow or deny network traffic to subnets and NICs. ... take advantage of an Azure architecture diagram tool like Cloudockit. Cloudockit will automatically generate your diagrams by finding the elements in your infrastructure. It can document more than 75 ...
An architecture diagram is a diagram that depicts a system that people use to abstract the software system's overall outline and build constraints, relations, and boundaries between components. It provides a complete view of the physical deployment of the evolution roadmap of the software system.
High-Level HA Architecture for VPN Instances 2. The diagram template below is of an HA design for the VPC component of the network. Like in the 3 rd example template, this one also shows the setup and the configuration of VPN instances, although there are only 2 instances here. In order to create a fully redundant VPN connection, these two instances need to be monitored so as to keep track of ...
Cloud Computing security architecture is categorized into frontend and backend, along with an amalgamation of the event-driven architecture and the service-oriented architecture in Cloud Computing. Frontend is a user/client-facing architecture. It comprises client-side interfaces and applications necessary to access Cloud Computing platforms.
Cisco Network Diagram Computer And Networks Solution In 2021 Computer Network Network Infrastructure Network Architecture. Pin On Wiring Diagram. Network Diagram Example Firewall Diagram Design Networking Small Business Network. Network Diagram Example Large Multi Protocol Network Computer Network Networking Diagram.
On-premises connectivity: In our architecture diagram, ExpressRoute is used. ... For example, to require incoming remote desktop connections to originate only from the corporate network, simply add a network security group to the virtual network on the remote desktop gateway. The only additional security consideration is the level of ...
Hi, Recently, I built the Azure Solution Architect Map aimed at helping Architects finding their way in Azure. Given the unexpected success and the very positive feedback I received, I decided to come up with other maps, namely the Azure Security Architect Map, the Azure Infrastructure Architect Map and the Azure Application Architect Map.. Here are all the maps in my series of Architecture Maps:
The json-asff format comes in handy for integration with AWS Security Hub. Containing network access Building a network diagram. We need a network diagram to assess the architecture of the cloud environment. It might be difficult for teams to have an updated network diagram, and due to the dynamic nature of the cloud, you might not know what ...
Other Documentation. Tenable.sc Large Enterprise Deployment Guide. Tenable Continuous Network Monitoring Architecture Overview Diagram. Tenable Professional Services Scan Strategy Guide. Compliance Checks Reference. CIS Controls Assessment Specification. Tenable Products Plugin Families.
High level SASE Architecture. In this new paradigm, IT requires a simple and reliable approach to protect and connect with agility. This is forcing a convergence of network and security functions closer to users and devices, at the edge—and is best delivered as a cloud-based, as-a-service model called secure access service edge (SASE).
Hence, this network architecture design is recommended for customers wanting to adopt Cloud Adoption Framework data management and analytics. If extra network policies need to be enforced within the data platform, it's advised to use network security groups instead of central network virtual appliances. Meshed network architecture conclusion
Microsoft online services systems, dependencies, and external connections are documented in Microsoft online services' information security architecture. Both the information security architecture and corresponding data flow diagrams are reviewed and updated annually at a minimum, as well as whenever significant changes are made to the system.
October 24, 2021. High Level Example Of Hub And Spoke Vdc Networking Cloud Infrastructure Cloud Diagram. Microsoft Azure Architecture Solution Azure Computer Network Solutions. Azure Network Diagram Use Azure Diagram Tool By Creately To Draw Your Azure Network Diagram Azure Network Diagram Tool Hel Diagram Fuse Box Widebody Ferrari.





















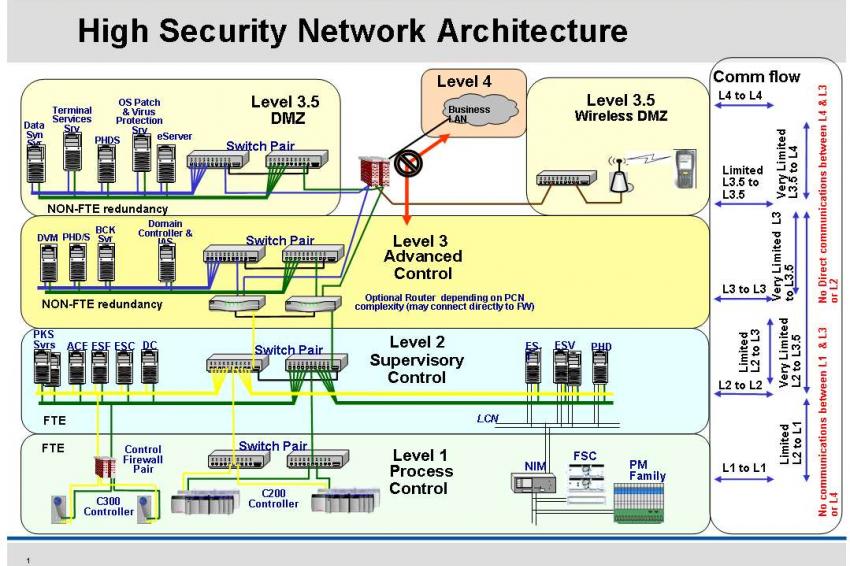


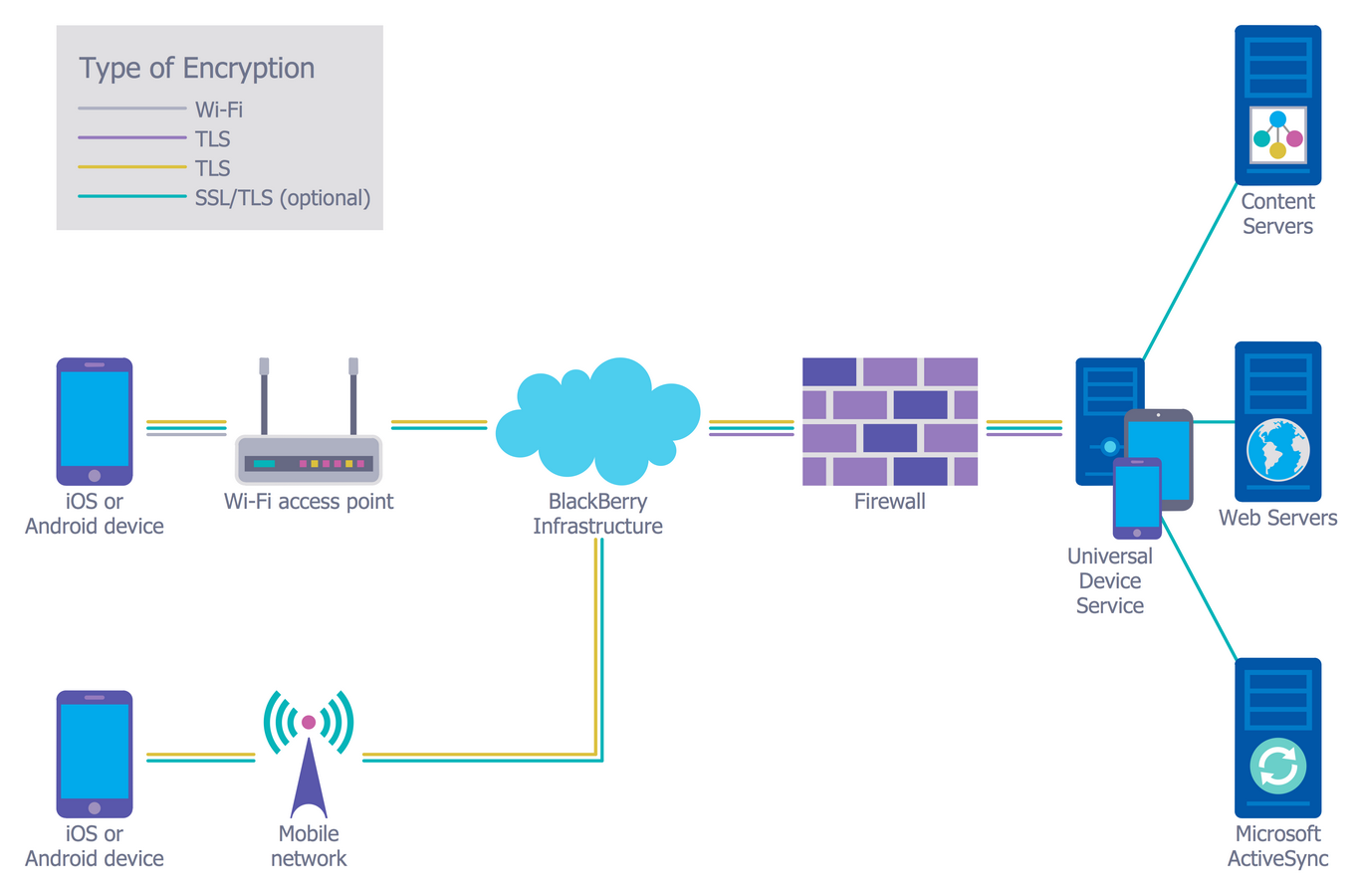
0 Response to "38 network security architecture diagram"
Post a Comment